
I am Prateek Gianchandani. I have interests in Reverse Engineering, Mobile and Browser Security, and i am the founder of 8ksec. I hope you enjoy the content in this Blog.
recent articles
iOS Application Security Part 41 - Debugging applications using LLDB
Apr 28, 2015
In this article we will learn about the LLDB debugger used by Apple’s Xcode for debugging applications, understand why it is better for security testing, and then learn how to use it to debug iOS applications. The following excerpt is from Apple’s documentation. LLDB is Apple’s from the ground up replacement for GDB, developed in close coordination with the LLVM compilers to bring you state-of-the-art debugging with extensive capabilities in flow control and data inspection. Starting with Xcode 5, all new and preexisting development projects are automatically reconfigured to use LLDB. The standard LLDB...
iOS Application Security Part 40 - Testing apps on your Mac
Apr 28, 2015
In this article, we will discuss the extent to which you can test applications on your Mac rather than the device. This could be useful for many reasons, sometimes you may not have a jailbroken device but want to get a POC for a vulnerability. We will discuss what are the things you can and cannot do. To test the application on your system, you will need to have Xcode installed on your system and you will run the applications on the iOS simulator. Installing ipa files from iTunes on your simulator Sadly, there...
Damn Vulnerable iOS App solutions free for download
Apr 3, 2015
I have decided to give away the solutions for DVIA for free. The reason for this has been too many people coming up with queries for the solutions and i believed giving away the solutions for free would really benefit the infosec community. It has taken me a lot of nights and hard work to create this project and specially the solutions. If you think this project has been useful to you and your organization, please consider making a donation to this project. You can donate to this project and download the solutions for...
Android Application hacking with Insecure Bank Part 4
Mar 29, 2015
In this article, we will look at a very handy framework for analysis of android applications named Drozer. Drozer is a very useful tool as it eliminates the need for having seperate tools for performing different security checks in an android application. It has a list of modules that you can use to interact with the application using Android’s Inter-Process communication. Additionally, you can also install exploits and use it to exploit an android device. The main purpose of this article is to make sure you are familiar with drozer so we can use...
Android Application hacking with Insecure Bank Part 3
Mar 28, 2015
In this article, we will look at attacking components in Android applications, starting with activities. But first, it is essential to understand what Android application components are. Android application components are the essential building blocks of an Android application. The behaviour and interaction between these components is defined in the manifest.xml file in the application. Mainly there are 4 types of components and it is important to understand their purpose and function. The description of the 4 components given below has been taken from this link. Activities - They dictate the UI and handle...
iOS Application Security Part 39 – Sensitive information in memory
Mar 24, 2015
In this article, we will look at analyzing the memory contents of an iOS application. iOS applications may store sensitive information like passwords, session IDs etc in the memory of the application without releasing them. In some cases, releasing these variables may not be an option. For e.g, it might be required for the application to send an authentication token with every request and hence there has to be a reference to it in the memory somewhere. Even though these variables might be encrypted when stored locally in the application, these variables will be...
Android Application hacking with Insecure Bank Part 2
Mar 23, 2015
In the previous article, we looked at setting up a mobile pentesting platform for Android applications. By now, you must have set up an emulator using genymotion and installed all the android command line tools along with some other additonal tools (drozer, dex2jar, apktool). In this article, we will look at some information gathering techniques. We will see how we can decompile an application to its java source, analyze the signature of the application and many more things. At this point, i would also like to mention that if you are looking for a...
iOS Application Security Part 38 - Attacking apps using Parse (Guest Lecture by Egor Tolstoy)
Jan 24, 2015
This is a guest lecture by Egor Tolstoy. Egor is a full-time iOS developer working at Rambler&Co and living with his lovely wife in Moscow, Russia. In his spare time he investigate iOS applications for different vulnerabilities and blogs about my research. [Parse](http://parse.com/) is a wonderful BaaS which helps with setting up backend infrastructure for your mobile application as fast as possible. Maybe just because of this simplicity many developers forget about a number of new security issues and vulnerabilities. 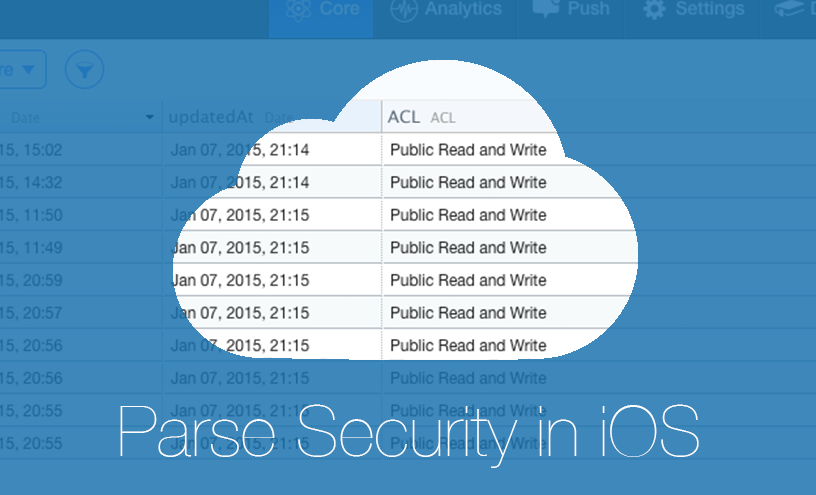 For those who don’t know what this service is, let’s make a brief...
iOS Application Security Part 37 - Adapting to iOS 8
Dec 20, 2014
In this article we will look at all the things you need to do to set up a pentesting platform on iOS 8 and be comfortable with using all the tools. Jailbreaking your device If your device is running iOS 8.1 or earlier, you can use pangu to jailbreak your device. The process is pretty straightforward. We will not be covering jailbreaking your device in this article but if you want to know how it is done, you can read this article. Note: I was getting an error with Pangu saying that there was...
Damn Vulnerable iOS App v1.4 launched
Dec 1, 2014
I am so excited to release the latest version of Damn Vulnerable iOS app for iOS 8. Up till now, DVIA has been downloaded more than 75000 times and i can’t wait for the count to reach 6 digits :-) Following vulnerabilities and challenges have been added in the latest version. Sensitive information in memory Webkit Caching (Insecure data storage) Certificate pinning bypass You can download the latest version from here. The source code is available on the project’s github page here. Manual Installation The easiest way is to install the application from Cydia....
Android Application hacking with Insecure Bank Part 1
Nov 24, 2014
In this article series, we will learn at various concepts of Android application security while exploiting a vulnerable app InsecureBankv2. We will be looking at all the concepts from a noob’s perspective and hence i would recommend this blog series to beginners as well. However, the first thing to do is set up a proper mobile pentesting platform for android application testing. The first thing to do is download the Eclipse ADT bundle. You can then follow the instructions here to install the ADT bundle. Once this is done, make sure you install the...
iOS Application Security Part 36 – Bypassing certificate pinning using SSL Kill switch
Nov 3, 2014
In this article, we will look at how we can analyze network traffic for applications that use certificate pinning. One of the best definitions i found of certificate pinning is mentioned below. It is taken directly from this url. By default, when making an SSL connection, the client checks that the server’s certificate: has a verifiable chain of trust back to a trusted (root) certificate matches the requested hostname What it doesn’t do is check if the certificate in question is a specific certificate, namely the one you know your server is using. Relying...
Wifite Walkthrough part 2: Cracking WPA access points
Oct 27, 2014
In this article, we will look at cracking access points using WPA-PSK or WPA2-PSK using Wifite. If you have used tools like airodump-ng, aircrack-ng etc to crack WPA access points before, you would know that the required thing to successfully crack a WPA-PSK network is a captured WPA four-way handshake. More details about the WPA four-way handshake can be found on this wikipedia page. As mentioned in the previous article, there is a bug in Wifite that may or may not be there in your particular version of Wifite. The bug basically doesn’t aireplay-ng...
Wifite Walkthrough part 1: Cracking WEP access points
Oct 27, 2014
In this article series, we will look at a tool named Wifite suitable for automated auditing of wireless networks. Most of you who have experience in wireless pentesting would use tools like airmon-ng, aireplay-ng, airodump-ng, aircrack-ng to crack wireless networks. This would involve a sequence of steps, like capturing a specific numbers of IV’s in case of WEP, capturing the WPA handshake in case of WPA etc, and then subsequently using aircrack-ng to crack the password required for authentication to the network. Wifite aims to ease this process by using a wrapper over all...
iOS Application Security Part 35 – Auditing iOS Applications With iDB
Oct 18, 2014
In this article, we will look at another cool utility named iDB for pentesting iOS applications. Before that, i would like to apologize for coming up late with this article. A lot of you have been requesting articles on different topics and i promise that i will write on them soon :). So since we are best friends again, let’s dive into this tool. iDB is open source and you can download it from its Github page. You can then follow the tutorial here to know how to install it. Installation might take some...
iOS Application Security Part 34 - Tracing Method calls using Logify
Apr 18, 2014
In the previous articles, we have seen how applications like Snoop-it can trace method calls specific to the application at runtime. This is very important in deducing the flow of the application. The same process can be performed by using a perl script named Logify.pl that comes installed with Theos. The script takes input as a header file and generates the hooking code that we can add in our tweak. We can also specify the classes we want to check. Once the tweak is installed on the device, whenever a method for that particular...
iOS Application Security Part 33 - Writing tweaks using Theos (Cydia Substrate)
Apr 18, 2014
In some of the previous articles in this series, we have looked at how we can modify the behaviour of an application by patching it using IDA Pro, Hopper etc. However, doing this hasn’t been quite straightforward always. We can also use Cycript to modify the behaviour of an application by changing some of the method implementations, but the change isn’t permanent. This is where writing tweaks for an application comes in handy. A tweak is nothing but a run-time patch to an application using the Cydia Substrate framework. Cydia Substrate consists of 3...
iOS Application Security Part 32 - Automating tasks with iOS Reverse Engineering Toolkit (iRET)
Mar 25, 2014
While doing security audit of iOS apps, there are a lot of tasks that we have to repeat every time. This includes finding out the class information for the app, checking if the application stores any important data in plist files, analyzing the content in the database files etc. These tasks can be a little time consuming every time and so it doesn’t make quite a lot of sense to repeat them over and over again for every app. We have also looked at some tools like Snoop-it and iNalyzer that make our job...
iOS Application Security Part 31 - The problem with using third party libraries for securing your apps
Mar 18, 2014
In this article, we will talk about why we shouldn’t completely rely on using third party libraries for securing our apps. Usually, some of the things we try to do in our application are adding checks to detect piracy, jailbroken device etc. It is such a pain to write all the code from scratch which is why we usually resort to using third party libraries that can get the job done for us. In this example, we will be looking at a library named AntiPiracy which can be found on this url that aims...
How to distribute IPA file for jailbroken devices
Mar 12, 2014
So i have been getting a few queries on how to create an IPA file from Xcode and distribute it for jailbroken devices. Here is how i did it for Damn Vulnerable iOS App. First we need to run the application using Xcode on the device. This requires a valid provisioning profile. I am doing this on Xcode 5.x but on the previous versions of Xcode, it was possible to run the application on the device without a valid provisioning profile. Once the application is installed on the device, copy the .app folder from...